Introducing npm package SLSA provenance support
Not knowing where your software dependencies come from leaves your codebase vulnerable to breaches, exploits and supply chain attacks. Just since the beginning of 2023 we’ve seen many examples of actors attempting to inject malicious packages into open source consumers supply chains. With SLSA provenance attestations, users can verify an artifact’s build integrity to ensure that malicious parties have not created, tampered with or replaced the code they’re running.
We are excited to announce that deps.dev now shows SLSA provenance information for npm packages to provide more information and improve trust for package consumers. You can view the provenance information for supported npm packages on deps.dev — for example, deps.dev/npm/js-cookie.
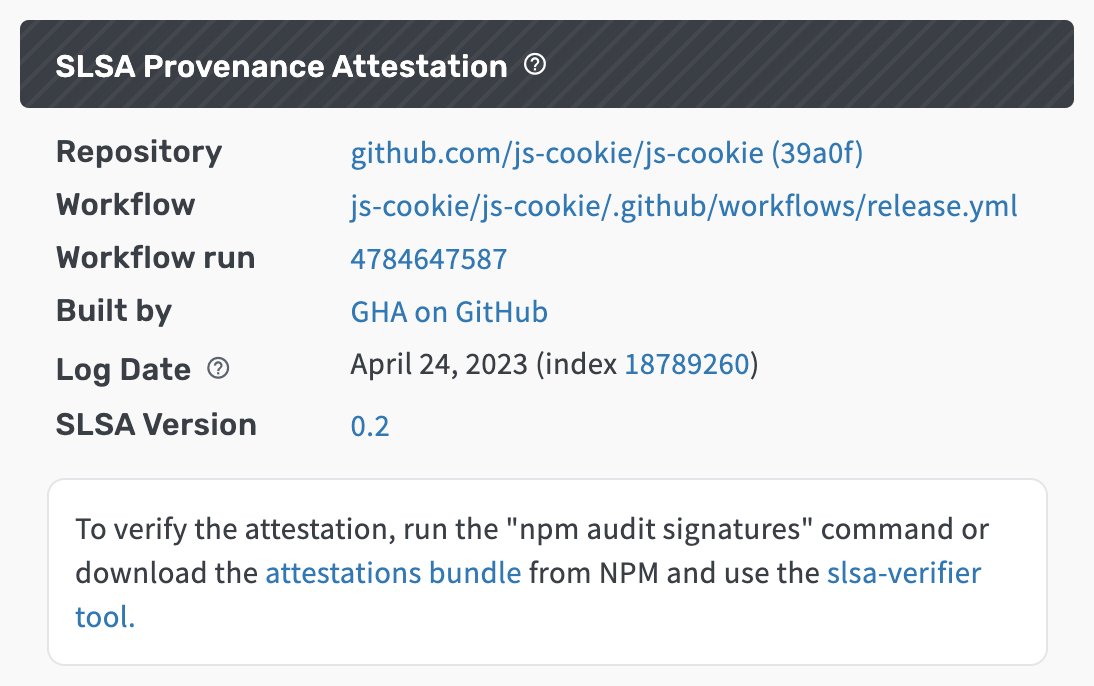
SLSA provenance is metadata about how a package was built and strongly links an open source package to the build system and source code used to create it. It is part of the SLSA framework for improving supply chain security. In the provenance attestation you can find:
- the repository and commit at which the version was built
- details about the workflow used to create the version
- how the version was built
- the date the attestation was integrated into the rekor transparency log.
npm recently announced the public beta for their integration with the Sigstore project. This allows package owners to upload cryptographically verifiable SLSA provenance attestations along with their packages. In the future, integrations with the npm CLI tool will automatically verify attestations on install, making working in npm more secure by default. (However, it’s important to note that not all npm packages will have these attestations and older versions will not automatically be republished. Further information is available in npm’s announcement).
It’s great to see npm working to make the open source ecosystem more secure and we hope to see other package managers follow suit! For more information about SLSA visit the SLSA homepage. Instructions are available for npm package maintainers who want to add SLSA provenance information to their packages.
